Monitored Security and performance are among the highest concerns if you're running any business or providing any service, especially in a VPS Hosting where the confidential data of your business and clients is stored. iptables are perhaps one of the most efficient means of managing network traffic, providing security the way you defined. This feature-rich firewall command enables you to filter and manage incoming and outgoing connections based on the rules you set.
Unless iptables are correctly configured, your server can be attacked, be subjected to unwanted traffic, and perform slowly. Mastering listing, editing, and deleting iptables rules will give you complete control over your network security and stop misconfigurations that can expose your server to vulnerabilities.
This tutorial will guide you on how to manage iptables rules effectively in Ubuntu Server 24.04 with concise examples and outputs so you can handle your firewall like a pro.
What’s Covered in this Tutorial:
How to Clear Packets and Byte Counters?
Is-required
Here, we assume you have installed the iptables command and are a sudo user running on your Ubuntu VPS Server.
If you have not installed iptables on your Ubuntu VPS, this tutorial will help you install and configure iptables rules.
How to List iptables Rules?
Before making any changes, it’s crucial to see the existing rules in your iptables configuration.
Output: Shows the rules we previously defined.
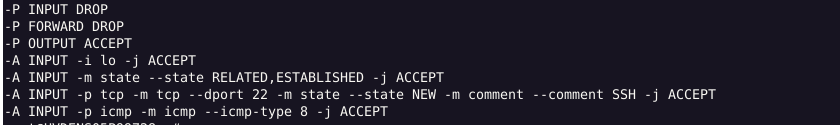
Here are different ways to list rules with explanations and expected outputs.
How to List Rules in a Table Format?
Output: Shows the rules we previously defined in a readable format.
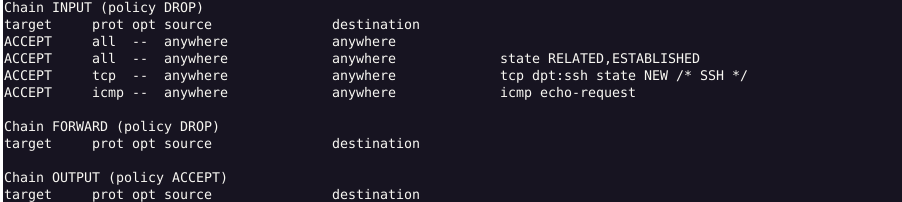
You can see the difference between the -S and -L commands.
How to List Rules with Line Numbers (Useful for Deleting or Modifying Rules)
Output: This shows the Rules by their line numbers, useful in deleting or replacing a particular rule by line.
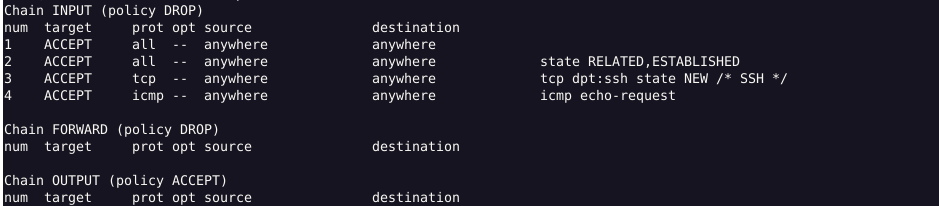
How to List Rules by a Specific Chain?
If you want to filter rules by a specific chain like INPUT, ACCEPT, or DROP.
Output: This shows the rules previously defined for the INPUT chain. (Output may differ as per the rules you defined.)
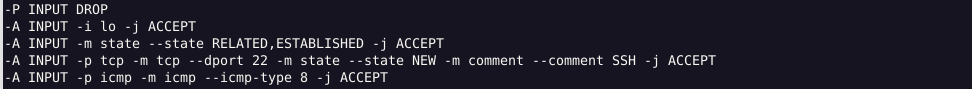
Output: This shows the rules previously defined for the INPUT chain in a table format.

Chain INPUT (policy DROP) : indicates the chain name (INPUT, in this case), followed by its default policy (DROP).
The header’s explained:
- target: If a packet matches the rule, the target specifies what should be done with it. For example, a packet can be accepted, dropped, logged, or sent to another chain to be compared against more rules
- prot: The protocol, such as tcp, udp, icmp, or all
- opt: Rarely used, this column indicates IP options
- source: The source IP address or subnet of the traffic, or anywhere
- destination: The destination IP address or subnet of the traffic, or anywhere
How to List Rules with Packets and Bytes Count?
The reason for tracking packet counts, byte counts, and interface details in iptables is network monitoring and troubleshooting.
- Helps understand how much data is flowing through specific rules, identifying heavy traffic sources.
- Security Monitoring – Detects unusual spikes in traffic (e.g., DDoS attacks, unauthorized SSH attempts).
Output: This shows the packets that matched the particular rule, the packet size in bytes, etc.
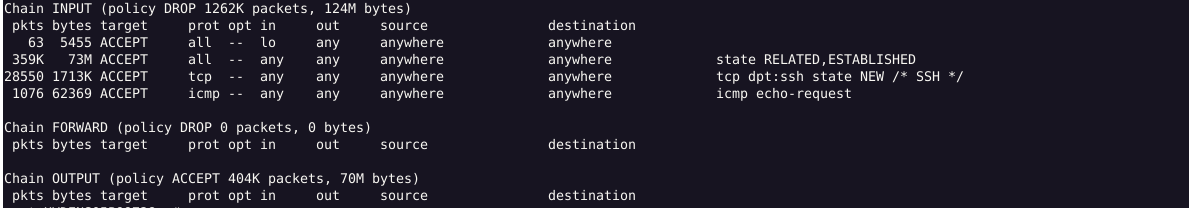
Headers Explained:
pkts (Packets): Number of packets that matched the rule.
bytes (Bytes): Total size of matched packets in bytes.
in (Incoming Interface): The interface from which the packet is coming.
out (Outgoing Interface): The interface where the packet is going.
state: Connection tracking states (NEW, ESTABLISHED, RELATED).
How Resetting Packets and Byte Counters Helps in iptables?
It is helpful if you want to see if your server is receiving new traffic that matches your existing rules.
How to Clear Packets and Byte Counters?
Use the -Z option if you want to clear the packet and byte counters for your defined rules:
To clear only the INPUT chain counters, run this command:
How to Save iptables Rules?
This saves the current firewall rules to a file so you can restore them later.
Why and How to Replace Existing iptables Rules?
As your server’s security needs evolve, you may find that some iptables rules need to be modified instead of simply adding new ones. Replacing rules is essential to prevent conflicts, optimize traffic flow, and maintain a clear firewall setup.
You might need to replace an iptables rule when:
- A rule was incorrectly defined and needs correction.
- Network policies have changed, requiring different filtering rules.
- You want to optimize your firewall rules for better security and performance.
Steps to Replace an Existing Rule:
1. Find the rule number:
2. Delete the existing rule by its number:
3. Add the updated rule:
This example blocks all traffic from 192.168.1.159.
Firewall rule replacement allows your server to stay secure while preventing unnecessary complications due to duplicate or conflicting entries.
Why and How Should We Delete iptables Rules?
With time, rules for iptables can turn out to be obsolete, redundant, or just plain wrong. Having unnecessary rules in your firewall can increase processing times, cause unwanted blocking of traffic, or even present security risks.
You should consider deleting iptables rules when:
- A rule is no longer relevant due to changing network policies.
- A temporary rule was applied and is no longer needed.
- An incorrect rule was mistakenly added.
- You need to reset the firewall rules to start fresh.
1. Delete a Rule by Its Line Number
The above command removes the 2nd rule from the INPUT chain.
2. Delete a Rule by Specific Match
This deletes the rule that blocks 192.168.1.169.
3. Delete All Rules in a Specific Chain
Clears all firewall rules from the INPUT chain.
4. Delete a Specific Chain (if custom-created)
Deletes the user-created (CUSTOM_CHAIN) if it exists.
5. Deletes all iptables Rules (FULL RESET)
Completely flushes all firewall rules even if you are using iptables - persistent.
From hackers, bots, and unwanted traffic clogging up your resources, you need a firewall that YOU control.
Properly configuring iptables is essential for the security of your VPS. Without a well-maintained firewall, your server is vulnerable to unauthorized access and resource-draining traffic. Regularly reviewing and updating your iptables rules is crucial for protecting your valuable data.
Learning how to list, edit, and delete rules ensures that your server remains secure and optimized. Make a backup of the rules before making any drastic modifications, and if in doubt, test changes in a staging environment beforehand.
Still confused or need help? Check out our Affordable VPS Hosting plans, where we provide pre-configured firewall settings to secure your server from day one!



