For any website, it is necessary to have a firewall (a checkpoint between networks). After passing through the firewall, a website or an IP can access the server & its applications. However, a firewall is the first layer of security. To ensure multiple levels of security, it is recommended to configure iptables which provide a facility to set rules for incoming or outgoing traffic.
Iptables are a critical firewall utility with Linux systems, bringing massive security by filtering incoming and outgoing network traffic based on specific pre-set rules. It allows the system administrator to control the server's entry and exit traffic. Therefore, it is a vital tool for keeping your Ubuntu VPS secure against unauthorized users - DDoS- and other malicious attacks.
This guide will take you through the step-by-step process of implementing iptables rules on your Ubuntu VPS version 24.04, ensuring your server is secured against possible threats.
Why Set up iptables in Ubuntu?
Iptables are essential to protect the Linux server from many cyber threats. Through the help of iptables, one can ensure no unauthorized access is granted by allowing only specific traffic to enter/leave the server.
How Does Setting iptables Rules Help?
- Protect against brute force attacks, DDoS attacks, and port scanning.
- Lower the chances of malware infection due to some bad traffic.
- Enhance network performance by filtering out unwanted traffic.
- Allow administrators to create their own traffic rules for both inbound and outbound traffic on the levels of various protocols, ports, and IP addresses.
Proper configuration ensures your server remains secure and, at the same time, functions effectively in a controlled network environment.
How Do iptables Work?
Iptables work by inspecting incoming traffic through pre-defined firewall rules. When the incoming traffic reaches the server, it will be verified by iptables if it fits any predefined criteria. If a match is found, iptables will take appropriate action. Without a matching rule, iptables uses a default policy to assign traffic. Generally, iptables would allow anything that fits the rules and block anything that doesn't by default.
How do I configure IP tables in Ubuntu OS?
You need a VPS with Ubuntu Linux OS and sudo privileges to set iptables rules.
Recommended:
- Type the following command to list the available packages:
sudo apt update
- To upgrade the latest versions of all the packages, type the command:
sudo apt upgrade
How to install iptables in Ubuntu VPS?
There are two commands to install iptables:
- The below command simply installs iptables and saves rules (temporary) until you reboot the system.
sudo apt install iptables
- The above command installs and saves rules permanently, even after a system reboot.
sudo apt install iptables-persistent
|
Command |
Function |
Persistence |
|
sudo apt install iptables |
Firewall management tool |
❌ No persistence (rules lost after reboot) |
|
sudo apt install iptables-persistent |
Automatically saves and restores firewall rules |
✅ Yes (Rules restored after reboot) |
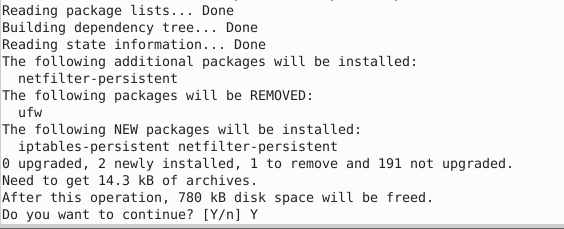
After you type the above command, it will ask for the removal of ufw (Uncomplicated Firewall):
Click ‘Y’ to proceed with the installation of iptables-persistent.
Output of the iptables-persistent command:
How to Verify iptables Installation?
After installing iptables through the above commands, verify installation by typing the command:
Output: shows the latest version of iptables installed
![]()
How to Disable UFW (Uncomplicated Firewall)?
# Only needed with iptables (Optional)
This command is used to uninstall ufw completely:
Output:-
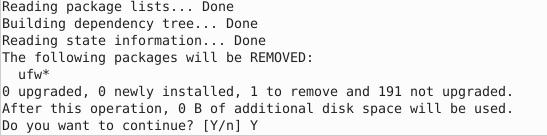
To remove any packages or dependencies of the uninstalled packages like ufw:
How To Define the iptables Rules in Ubuntu VPS?
How to See Any Predefined Rules for iptables
First of all, check for any pre-defines iptables rules in your VPS by typing the command:
-v – shows detailed outputs like packet count, byte count, etc.
We are now ready to define the iptables rules:-
# Allow all incoming traffic temporarily (default policy)
The above command allows everything for incoming traffic temporarily before setting rules.
# Flush (remove) all existing rules
It deletes all the current or previously defined, which is helpful while creating or defining new rules from scratch.
# Delete any custom chains
It removes all the custom UDF (User Defined Rules) rules.
# Allow loopback traffic
It allows local traffic (traffic generated from the internal system processes like MySQL on 127.0.0.1)
# Allow incoming traffic for established and related connections
The above command allows incoming packets that are part of existing or related connections (like replies from a web server or SSH session).
# Allow SSH connections
It allows new incoming SSH connections on port 22 from any IP address.
# Allow ping requests (ICMP echo)
It allows ping requests so the server can be tested for connectivity.
How Do You Block All Other Ports?
Always remember to use the DROP chain policy after accepting the required ports.
# Allow all traffic on the loopback interface (important for internal processes)
# Allow established and related connections (prevents breaking existing connections)
# Allow SSH (Port 22) - Prevent getting locked out
# Allow HTTP (Port 80) - If running a web server
# Allow HTTPS (Port 443) - Secure web traffic
Once you add the required ports above, you can block all other ports that are not mentioned by you.
INPUT DROP: Drops any incoming traffic that is not explicitly allowed.
How to Forward Traffic in Ubuntu?
FORWARD DROP: Blocks any forwarded packets.
How do you allow all outgoing traffic in Ubuntu?
OUTPUT ACCEPT: Allows all outgoing traffic.
How Do I Block an IP?
If you want to allow IPs only from trusted sources, you can do that with the help of this rule:
How Do I Allow an IP?
You can even allow a range of IP’s with the help of this rule:
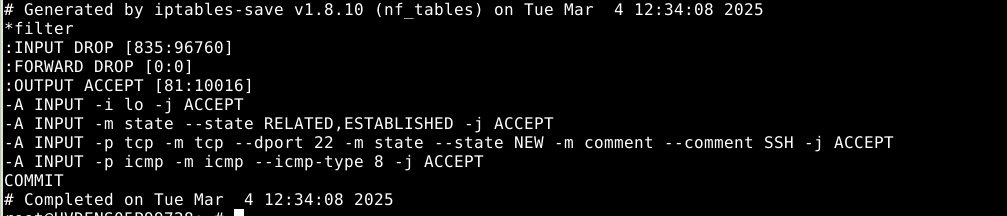
How to Check the Rules You Defined Through iptables -persistent?
This file stores IPv4 firewall rules that are automatically loaded at system startup if iptables-persistent is installed.
Run this command to check your rules are defined in the file:
Output:-
How to Edit/Replace the Existing iptables Rules?
To Edit or Replace specific rules in iptables, use the command:
First of all, list the iptables rules with their line number :
This command helps edit a specific rule as you don't need to reset all the existing rules to add a single.
Syntax:
Example:
How to Reset the iptables Rules Defined?
Resetting rules will permanently clear all the rules you defined, but be sure to reset only when you want to add new rules from scratch.
Command for resetting iptables:
While defining rules, utmost care should be taken, and every command should be used cautiously while you create rules for your website traffic. Installing iptables is not much, but setting iptables rules helps with security hardening for your domains and clients. Contact our support team for any issues you may face while configuring iptables.



