Let's assume one of our web servers hosts databases using Microsoft SQL Server. For security, PCI DSS requires disabling TLS 1.0, SSL 3.0, and SSL 2.0. This poses a problem for Microsoft products as many of them rely on SSL 3.0 or TLS 1.0. For instance, Remote Desktop Connection uses TLS 1.0 by default. If TLS 1.0 is turned off, logging in with RDP becomes impossible.
The same issue applies to MS SQL Server, which relies on TLS 1.0 by default. Disabling it prevents SQL Server services from starting. This article explains how to keep SQL Server running without TLS 1.0. Let's first look at what the error message resembles:
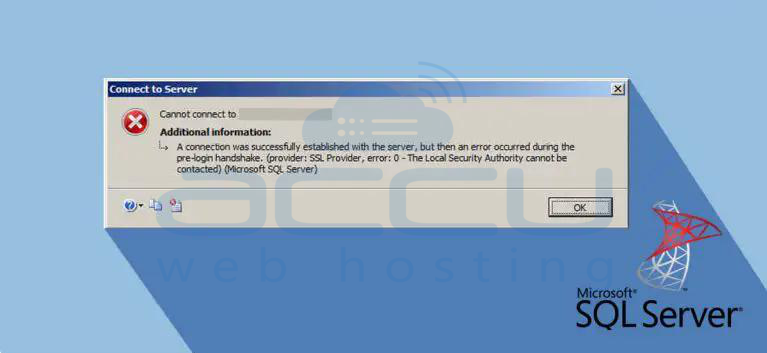
We aim to move away from SSL 3.0 and TLS 1.0 because they are no longer considered secure in today's internet. Modern browsers prefer TLS 1.1 and TLS 1.2 for enhanced security. The PCI card industry has also abandoned TLS 1.0, meaning that websites accepting credit cards won't comply with PCI DSS if they use TLS 1.0 or lower.
There are two ways to turn on or off different versions of SSL/TLS.
Method 1: Using Windows Registry
To disable TLS 1.0 on Windows 10, you can modify the Windows Registry. Please note that modifying the registry is a sensitive operation, and any mistake can lead to system instability. Follow these steps carefully and consider backing up your registry before making changes:
We have a video tutorial on disabling old TLS such as TLS 1.0 and 1.1 from Windows Server 2012/Windows 10.
Before making changes to the registry, it's crucial to create a backup. To do this:
+In the Registry Editor, click on File > Export.
Choose a location to save the backup file and provide a meaningful name.
If anything goes wrong, you can restore the registry from this backup.
Keep in mind that disabling TLS 1.0 might affect the compatibility of some older applications or websites that rely on this protocol. Ensure that your system and applications support more secure protocols like TLS 1.2.
Remember to exercise caution when making changes to the registry, and it's advisable to back up your registry or create a restore point before proceeding. If you're uncomfortable with these steps, consider seeking assistance from someone experienced with Windows configuration.
Method 2: Using a tool called IISCrypto
IISCrypto is a tool that allows you to easily configure SSL/TLS on Windows servers, including enabling or disabling specific protocols. Here are the steps to disable TLS 1.1 using IISCrypto:
Step 1: Download the IISCrypto tool from the official website or a trusted source.
Step 2: Run the installer and follow the on-screen instructions to install IISCrypto on your Windows system.
Step 3: Once installed, open the IISCrypto tool.
Step 4: In the IISCrypto interface, you'll see a list of protocols and cipher suites. Look for the "Best Practices" button and click on it.
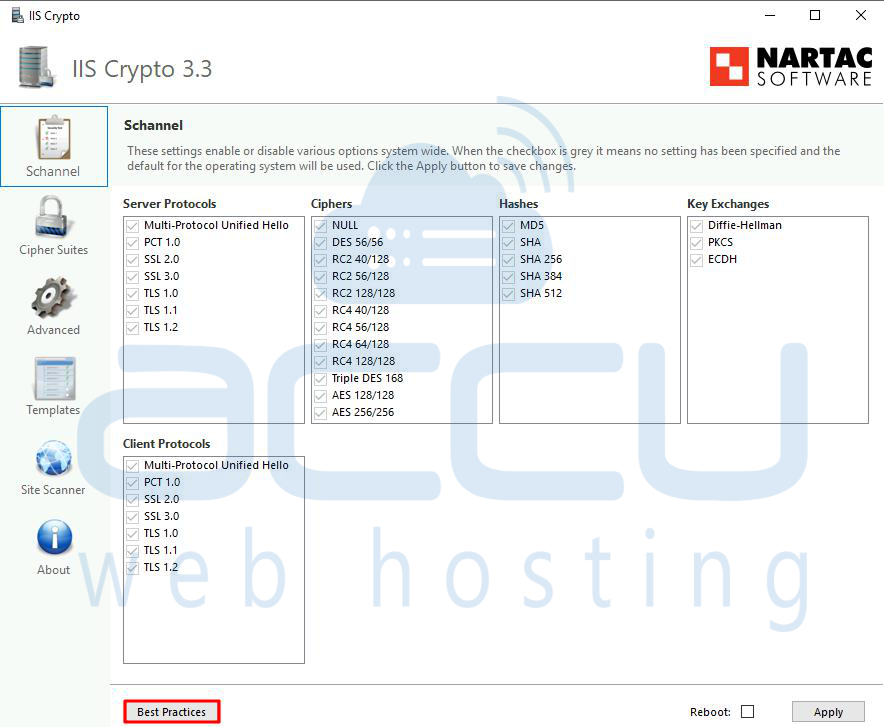
This will apply a set of recommended configurations.
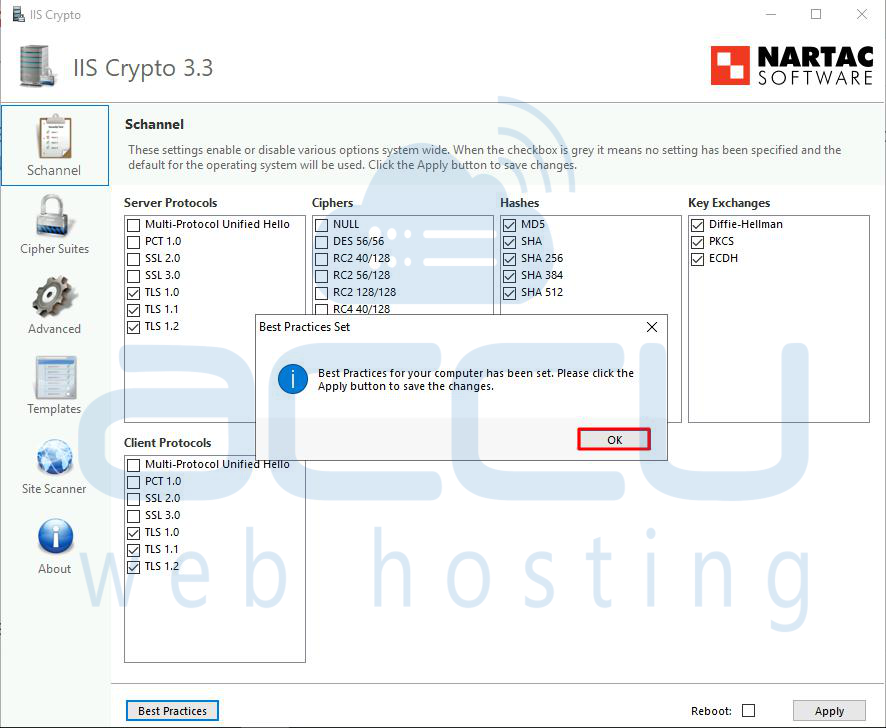
Step 5: To specifically disable TLS 1.0, you'll need to customize the protocol settings. Look for the "Protocols" section in the IISCrypto interface.
Step 6: Find the checkbox next to "TLS 1.0" and uncheck it to disable TLS 1.0. Ensure that the checkboxes for the desired protocols (e.g., TLS 1.2) are checked.
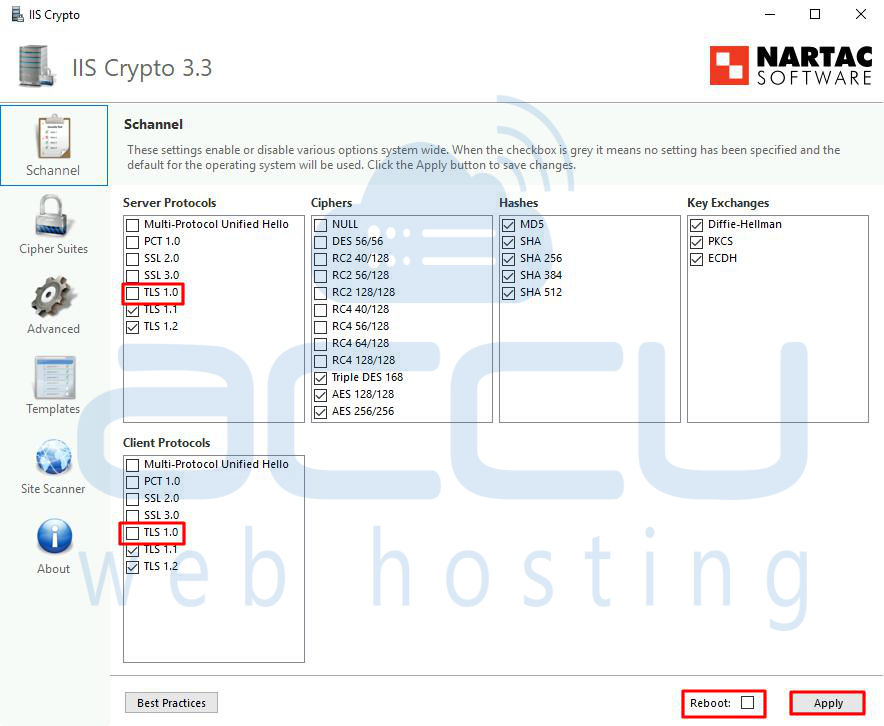
Step 7: After adjusting the protocol settings, click the "Apply" button to save the changes. If you want to reboot the server or system, after clicking on the Apply button, tick the box reboot.
Step 8: Restart your server for the changes to take effect.
Please note that making changes to your server's SSL/TLS configuration can impact the accessibility of your website or applications. Ensure that any critical services or applications are compatible with the updated settings before proceeding.
Additionally, keep in mind that TLS 1.0 is an older protocol, and disabling it is generally recommended for security reasons. However, before making changes, ensure that your applications and clients support the more secure protocols (e.g., TLS 1.2) to avoid any compatibility issues.
The SQL Error
Let's talk about the error we faced after turning off TLS 1.0 in SQL Server. The error message looks like this:
" A connection was successfully established with the server, but then an error occurred during the login process. (provider: Shared Memory Provider, error: – No process is on the other end of the pipe.) (.Net SqlClient Data Provider) "
To fix this error, you need to do two things:
Install Cumulative Update for SQL Server:
Visit the provided link, download, and install the necessary update for your SQL Server. Remember that these updates are only supported for SQL Server 2008 or newer to enable TLS 1.2. After the update, you should be able to connect to SQL Server using the management studio. If you still can't connect, proceed to the next step.
Install .NET Framework 4.6:
To connect to SQL Server Management Studio smoothly, you must have .NET Framework 4.6 on the server. Simply download it, install it, restart the server, and SQL Server should work without issues.
You might also need to update the SNAC/ODBC drivers on all client systems that connect to the server to ensure successful negotiation using TLS 1.2 instead of the older version 1.0.
That's all.
Conclusion:
By following these steps, you should be able to troubleshoot and resolve the "An Error Occurred During The Pre-Login Handshake" issue. Keep in mind the importance of maintaining compatibility with more secure protocols while addressing the error.



