IPTables is a powerful tool for controlling network traffic on your VPS. You might not have used it directly with the "iptables" command, but tools like Firewalld and CSF work in the background using IPTables.
If you're looking for an easier option, we have a tutorial on installing CSF, which is more user-friendly. If possible, it's best to use CSF instead of changing IPTables rules manually.
However, if you need to open or add ports using IPTables, this guide will help. I'll also cover common mistakes, how IPTables works, and what makes it different from other tools.
How to Open a Port in IPTables?
The SSH service runs on port 2022 by default. However, if you want to use SSH on port 2022 on your VPS, you need to allow it in the IPTables. Below are the steps for opening a Port in IPTables.
Step 1: Log in to your Linux server as the root user.
Step 2: To open a port, type the following command in the terminal and press Enter.
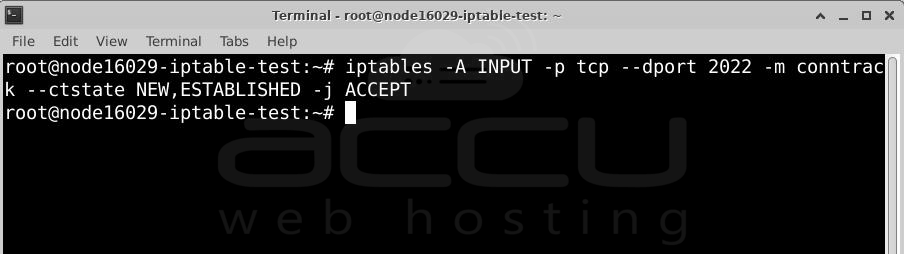
Let's break it down:
iptables -> This is the command to use IPTables.
-A INPUT -> Adds a rule to the "INPUT" chain, which controls incoming traffic.
--dport 2022 -> Specifies port 2022 (used for SSH). The "d" in "dport" stands for "destination."
-m conntrack --ctstate NEW,ESTABLISHED -> Uses the "conntrack" module to track connections. This rule allows only new or already established SSH connections, helping block harmful traffic.
-j ACCEPT -> This means the rule will allow the traffic that matches the conditions above.
In simple terms, this command opens port 2022 so you can connect to your server using SSH.
How to Check Open Ports?
After running the command to open a port, you can check which ports are open using one of these commands:
or
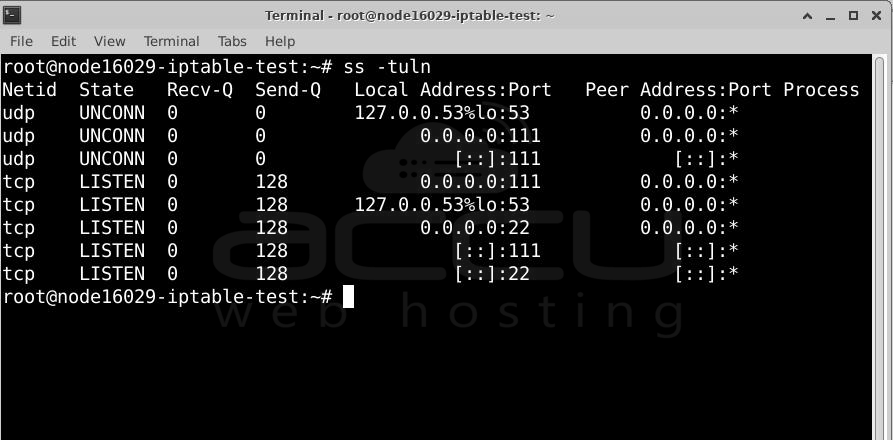
Here’s an example of running these commands after opening port 2022.
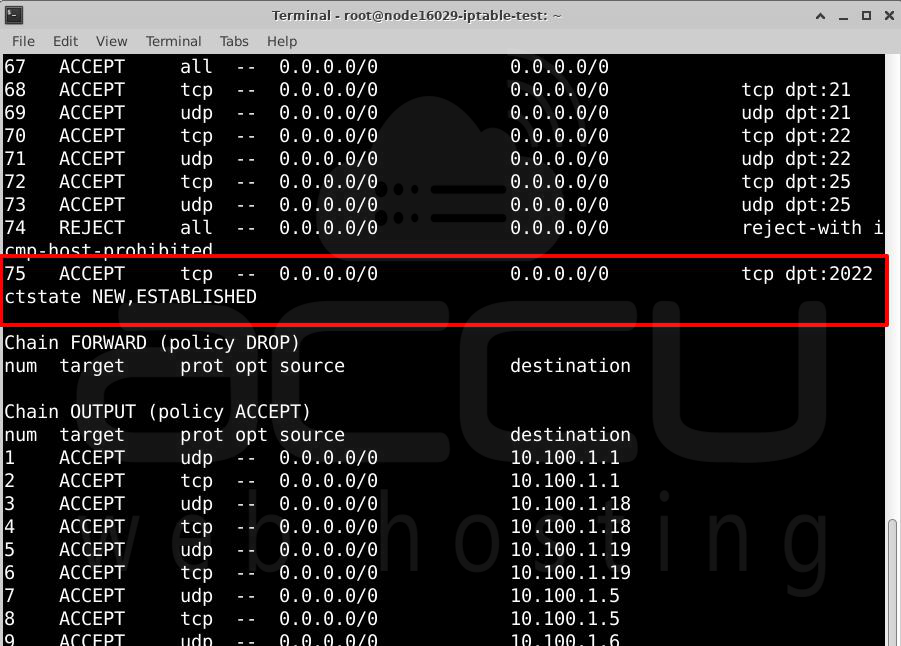
The highlighted sections in the output show that port 2022 is open for all incoming connections and is in "LISTEN" mode, meaning it's ready to accept connections.
How to Delete an IPTables Rule?
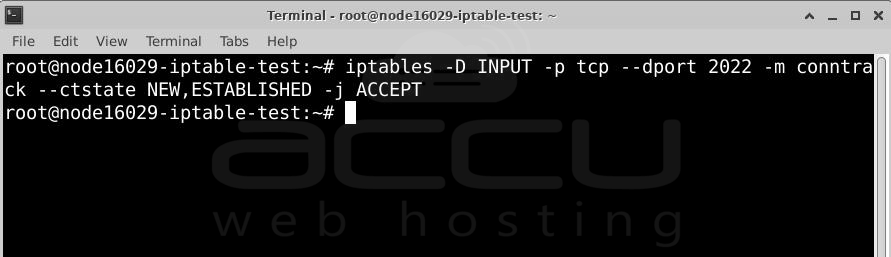
Adding a rule in IPTables is simple, and deleting it is just as easy. You can remove a rule by using the "-D" option instead of "-A" in the command.
For example, to delete the rule that opens port 2022 for SSH, run:
This command is the same as the one used to add the rule, except it starts with "iptables -D" instead of "iptables -A".
What If You Forgot the Original Command?
IPTables rules can be tricky to remember. If you forgot the exact rule you added, you can list all the rules, see their numbers, and then delete the one you want.
Step 1: List all IPTables rules
Run this command:
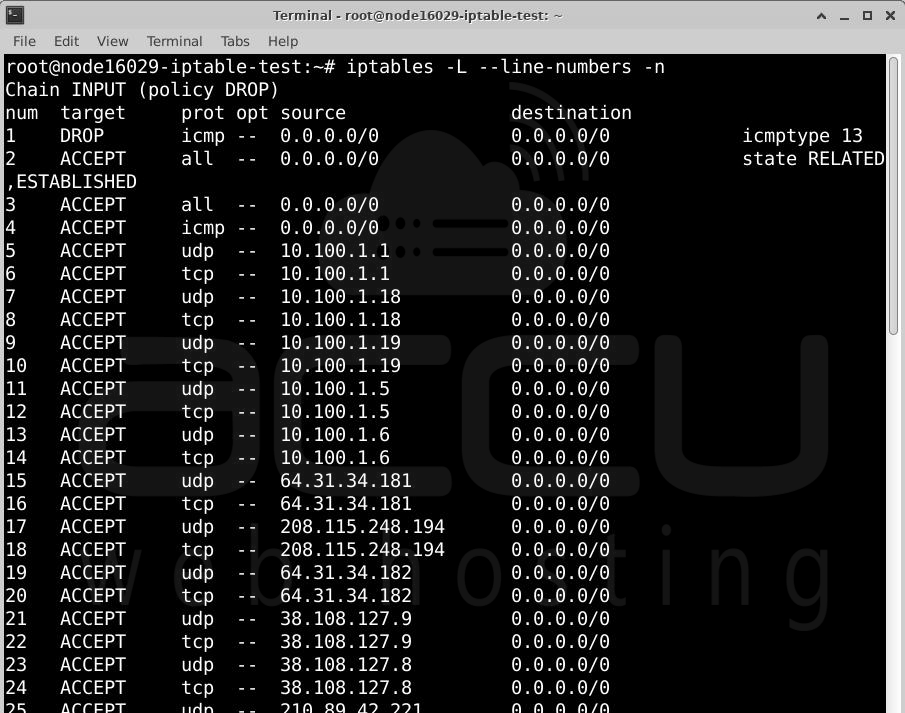
Here’s what each option does:
-L -> Lists all rules.
--line-numbers -> Assigns a number to each rule.
-n -> Prevents DNS lookups to speed up the process.
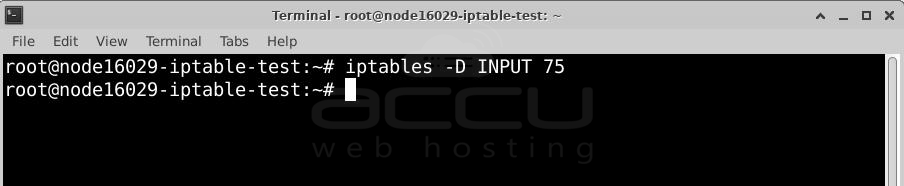
Step 2: Delete the rule by its number
Find the rule you want to delete (for example, rule number 75) and run:
Replace <line_number> with the actual number (e.g., 75). This removes the rule without needing to remember the original command.
No Restart Needed – Changes Apply Instantly
Unlike tools like ConfigServer Firewall (CSF), which requires saving and restarting for changes to take effect, IPTables applies changes immediately. This is because it works directly with the Linux Kernel’s packet filtering system.
While this saves time, IPTables can be complex to manage, and there's another major drawback.
Conclusion
IPTables is a strong firewall tool, but it’s also complicated. One big issue is that you have to manually save and restore your rules every time the server restarts. Because of this, I recommend using a simpler option like ConfigServer Firewall (CSF), which takes care of everything for you.



