SSH, or Secure Shell, is a way to connect to other servers safely. It uses keys to make sure it's really you and not someone else trying to get in. This is better than using just a password because it's harder for bad people to guess.
To set up this secure way of connecting, you need to do four things:
1. Generate RSA SSH Key Pair in AlmaLinux
2. Share the public part of the key with the remote Linux server.
3. Check if it works.
4. Turn off the option to log in with a password on the server.
1. Generate RSA SSH Key Pair in AlmaLinux
To start the process, we'll make a special pair of keys called RSA keys. These keys have one part that we keep secret (private) and one part we can share (public). We'll explain these keys more later.
To create these keys, you just need to run a command. It looks like this:
# ssh-keygen
OR if you want a stronger key, type:
# ssh-keygen -t rsa
The first command makes a good key for most uses. But if you want a very strong key, use the second command.
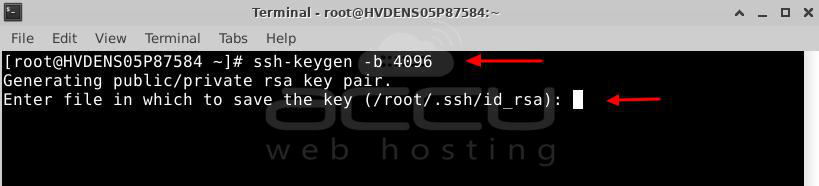
After you press ENTER, the server will ask where to save the keys. You can just press ENTER again to save them in the default place, which is usually a hidden folder called "~/.ssh."
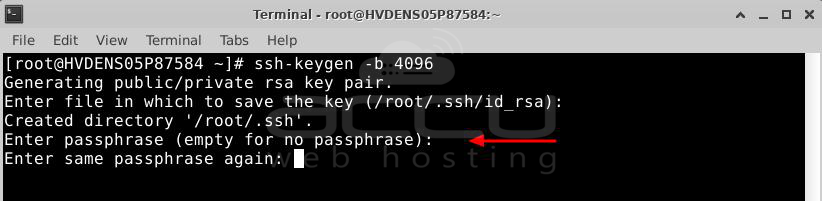
Then, the server might ask for a passphrase (a secret word). This is optional, but it adds extra protection. If you want to use your key without a password, just press ENTER here.
Here is the entire output of the command.
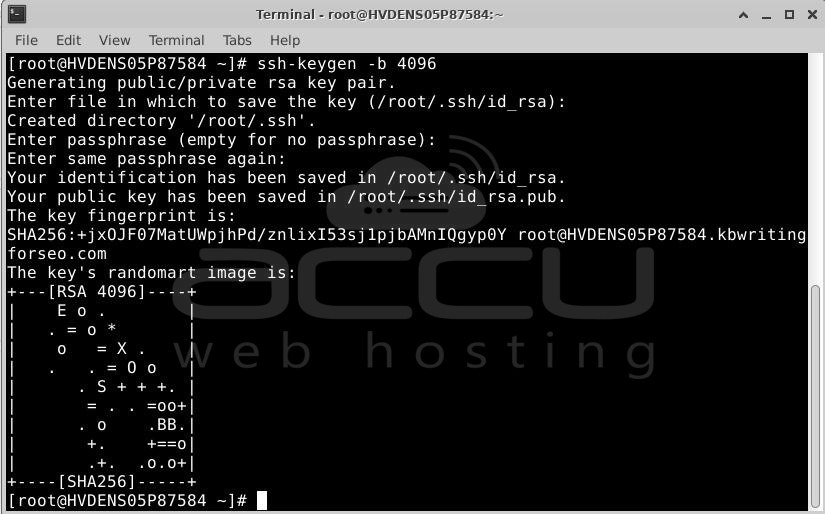
Now, your keys should be saved in the "~/.ssh" folder. You can check by typing:
$ ls -la ~/.ssh
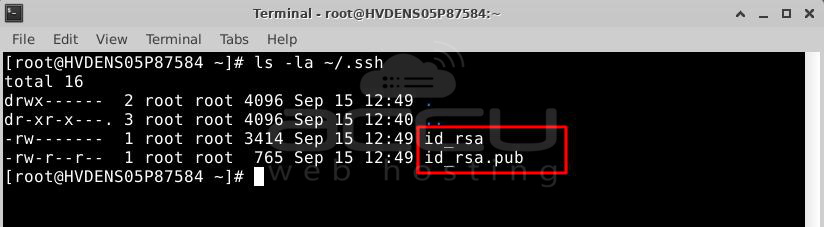
Here's something important:
- The "id_rsa" is your private key. It must stay secret. Never share it. If someone gets it, they can take control of your remote server.
- The "id_rsa.pub" is the public key. You can share this one freely. It's what you give to the servers you want to connect to.
2. Share the public part of the key with the remote Linux server.
The next step is to send the public key to the faraway server (we call it a remote server). You can do this by hand, but there's an easy command called "ssh-copy-id" that helps.
Here's how it works:
# ssh-copy-id user@remote-host-ip-address
In our example, we have a remote server with the IP address 23.XXX.XXX.XXX and a user named demovpstest.
So, to send the public key, you can type: $ ssh-copy-id demovpstest@23.XXX.XXX.XXX
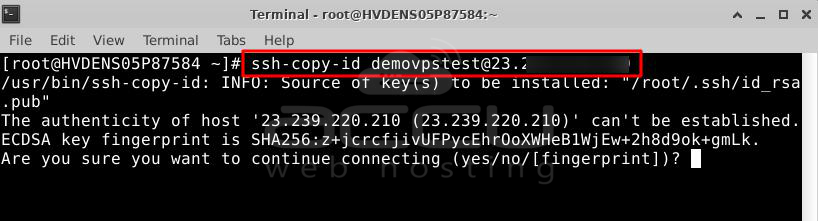
When you do this for the first time, the server might ask if you're sure you want to connect. Just type "yes" and press ENTER to say it's okay.
Then, it will ask for your password.
Once you type it and press ENTER, the public key goes to a particular file on the remote server in the "~/.ssh" folder.
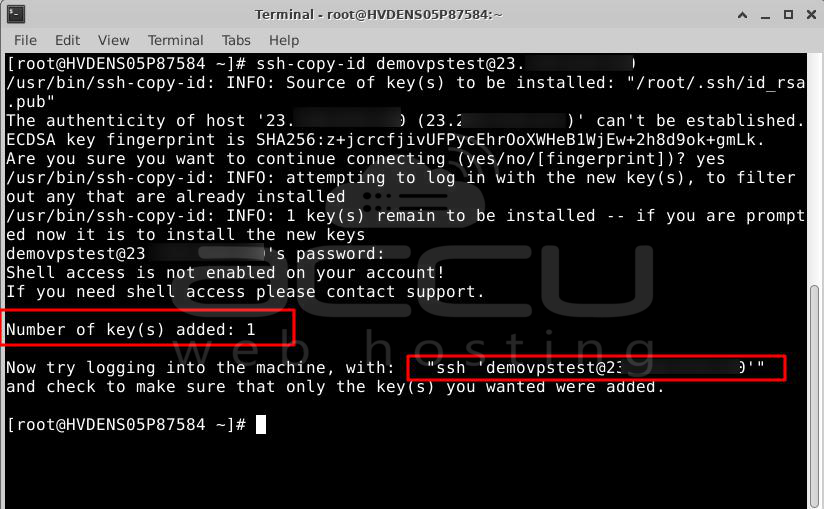
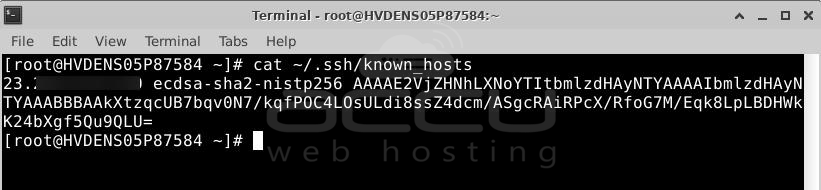
On your server, it also creates a file called "known_hosts" in the "~/.ssh" folder. This file keeps track of the remote servers you've connected to. You can see what's in it by typing:
# cat ~/.ssh/known_hosts
3. Check if it works.
SSH Passwordless Login to Remote Linux
Now that we have put the public key on the faraway server, we can log in there without needing a password for SSH.
To check if it works, we'll try logging in like usual:
# ssh demovpstest@23.XXX.XXX.XXX
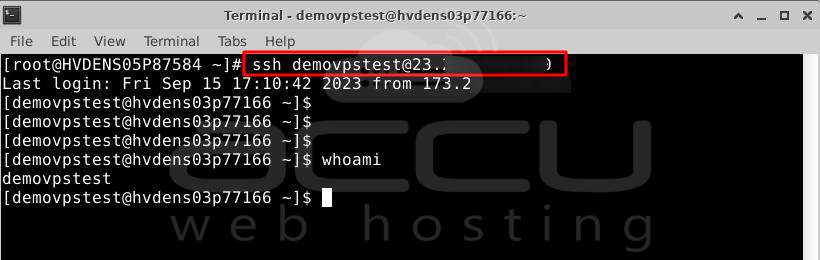
When you do this, you'll see that you're immediately inside the remote server. This means that we've set up SSH so you don't need a password anymore.
To make sure the public key is stored safely on the remote server, you can type:
$ ls -la ~/.ssh/

To see the actual file, you can use this command:
$ cat ~/.ssh/authorized_keys
4. Turn off the option to log in with a password on the server.
We're not finished yet. Right now, you can still log in using a password, which makes the remote server vulnerable to attacks where someone tries lots of passwords (brute-force attacks).
To make things safer, it's strongly recommended to turn off the password option. This way, you can only log in using your special SSH key, which is more secure.
Here's what you need to do:
Step 1: Open a file called "sshd_config" using a program called "vi."
# vi /etc/ssh/sshd_config

Step 2: Look for a line that says "PasswordAuthentication." If it's commented out (with a '#' at the beginning), remove the '#' and change it to say "no" like this:
PasswordAuthentication no
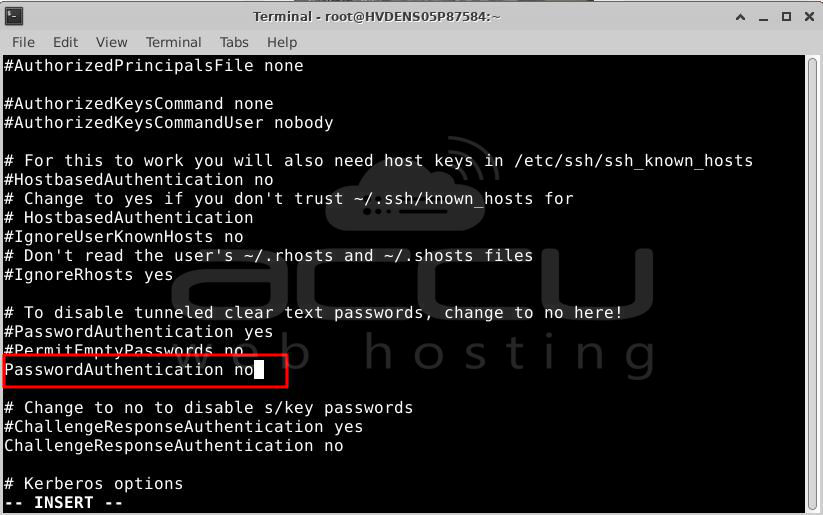
Step 3: Save your changes and exit the file.
Step 4: Finally, restart the SSH service to make the change take effect:
# systemctl restart sshd

Now, you won't be able to log in with a password anymore, only with your special key. This makes your remote server more secure.
Conclusion:
When you want to access an AlmaLinux 8 system from a distance, it's important to keep it super safe. By default, something called SSH lets you access the system by typing a password. But this isn't very safe because if someone guesses your password or finds it somehow, they can get in.
That's why it's better to use keys to get in. Keys are like secret codes. There are public keys (the ones you share) and private keys (the ones you keep secret). You can only connect to the system if your secret key matches one of the public keys on the system. You can even make your secret key extra safe by adding a password to it.
When you use keys, the system stops letting people in with just a password. It's a stronger way to protect the system.