The WordPress pharma hack quietly injects spam links (through database manipulation or file injection) into your pages, damaging your SEO and credibility. Search engines may blacklist your site, and visitors could see content that doesn’t belong there.
In this guide, we will learn how the WordPress pharma hack works and how to find and remove it to keep your site clean and secure.
What is a WordPress Pharma Hack?
A WordPress Pharma Hack is a form of malware attack that injects unauthorized pharmaceutical-related spam links to a website, usually without the owner's knowledge.
Hackers take advantage of vulnerabilities in old plugins, themes, or weak passwords to get access and alter a site's database, files, or search engine metadata.
The injected links are often used to promote illegal or counterfeit drugs and turn up in search engine listings, damaging SEO rankings and credibility and even resulting in blacklisting from Google.
How to find if your site is infected with WordPress Pharma Hack?
1. Look for Pharmaceutical Keywords in Google search
Check your site in any browser by adding 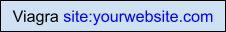 . Malicious (infected) sites might not be shown on the first page as per the policies of the webmaster, so scroll the page to three to four pages.
. Malicious (infected) sites might not be shown on the first page as per the policies of the webmaster, so scroll the page to three to four pages.
If you find suspicious pharmaceutical-related links associated with your website, it indicates that your site has been compromised by the Pharma Hack.
Other Keywords

2. Check Results As Google Bot
- Install a User-Agent Switcher extension on your browser (available for Chrome and Firefox).
- Open the webpage you suspect is infected.
- Edit the User-Agent to mimic Googlebot by selecting one of the following:
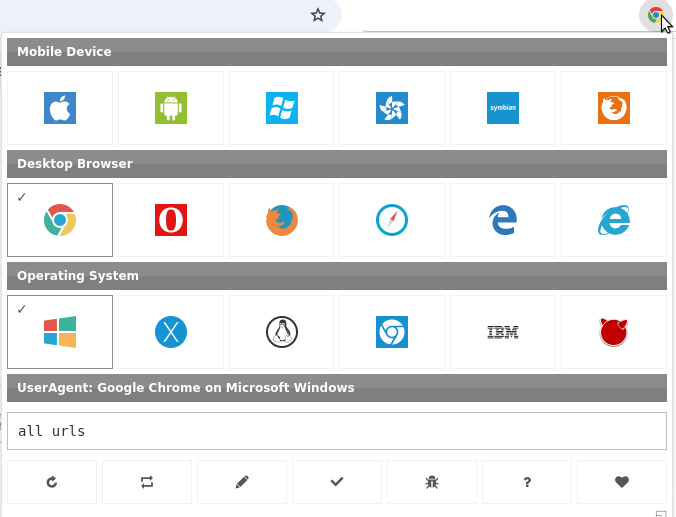
1. Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html) - Googlebot acts like a web browser to ensure that websites load properly.
2. Googlebot/2.1 (+http://www.google.com/bot.html) - It’s the version of Googlebot that is visiting your site.
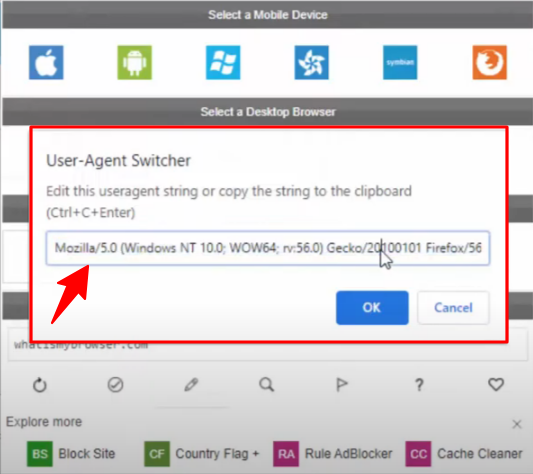
- Right-click on the page & choose "View Page Source."
- Look for unfamiliar scripts or hidden links directing visitors to pharmaceutical-related sites.
A User-Agent Switcher is an extension or tool that enables you to change your browser's identity when visiting a website.
With a User-Agent Switcher, you can simulate using a different browser, device, or even a search engine bot, such as Googlebot.
3. Scan Your Website
WordPress offers a plugin that scans every aspect of your site, including files, folders, databases, and cron jobs.
It identifies malware, hidden backdoors, and reinfection scripts that can cause malware to reappear.
4. Check for recently modified files
Then, check whether any of the core WordPress files have been modified. Files within the wp-admin, wp-includes, wp-content, and root directory (public_html) should typically not be changed, so it is crucial to ensure that attackers have not modified any content.
Also, review the recently modified files (within the last day or week) in your site's environment, including plugins & themes. These modifications could signal an active attack or the presence of a hidden backdoor that hackers might use to reinfect your site.
Hacked files often have names with .old, .class, or .cache, to look like plugin files. A dot (.) at the beginning makes them hidden unless you enable "show hidden files."
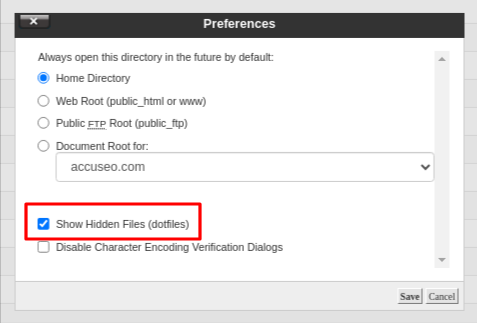
Check it from your File Manager (cPanel) > Settings.
Also, check for nav.php in the active theme's directory. This file may append wp-page.php to search engine requests and recreate itself after deletion. The header.php file contained injected code that loaded nav.php on every site visit, triggering the malware repeatedly.
Removing both nav.php and the malicious code in header.php successfully eliminated the infection, and the spam disappeared from search results.
5. Finding and Removing Suspicious Code
Check for unfamiliar code in your files because hackers inject malicious code that redirects users to a malicious website.
For Example:
<ul id="menu">
<li><a href="harmfuldomain.com">text</a></li>
</ul>
Attackers may hide code using Base64 encoding, making detection more difficult. You can search for Base64-encoded text in PHP files with the following command:
This command will generate a report named "b64-detections.txt" that you can review to identify any hidden malware.
How to Fix the WordPress Pharma hack?
1. Remove WordPress Malware Warnings
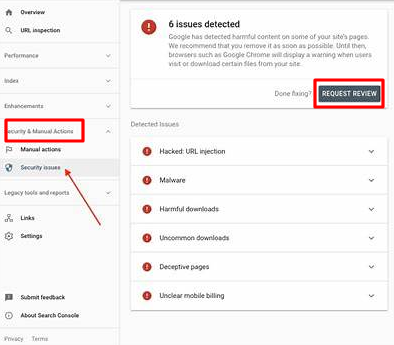
- Log into Google Search Console.
- Navigate to Security Issues > Security & Manual Actions, then select "Security Issues".
Here, you'll see any security problems identified on your site. Click on each issue to view details and affected URLs.
- After you resolve all listed issues, press the "Request Review" button.
Explain thoroughly how you have solved the problems. A well-elaborated explanation gives a higher chance of a successful review.
- Once you've detailed your fixes, click "Submit Request".
Important: Create a backup of your files, databases, plugins, and themes before making any changes. Even though the site is infected, having a backup ensures you can restore critical data and rebuild your site more easily if needed.
2. Clear the Temp Directory
The /wp-content/temp/ folder may be created due to a malware infection. Hackers utilize this folder to temporarily hold files that enable the installation of malicious software without corruption.
To delete it, go to /wp-content/temp/ within the cPanel's File Manager and remove its contents.
Also, check for hidden files, as discussed in step 4, when finding the WordPress pharma hack. Identify them and delete them.
3. Check the .htaccess File
The .htaccess file determines how your server handles requests. Hackers often alter this file to create backdoors and redirect traffic.
RewriteEngine On
RewriteCond %{ENV:REDIRECT_STATUS} 200
RewriteRule ^ - [L]
RewriteCond %{HTTP_USER_AGENT} (google|yahoo|msn|aol|bing) [OR] #checks for Google, Yahoo, msn, aol and bing crawler
RewriteCond %{HTTP_REFERER} (google|yahoo|msn|aol|bing)
RewriteRule ^(.*)$ hackfile.php?$1 [L] #redirects to a hack file
Why is this malicious?
1. Targets Search Engine Crawlers
- The above-mentioned condition checks if the visitor is a search engine bot (Google, Yahoo, Bing, etc.).
- This is a common technique used in pharma hacks to manipulate search results while keeping the site looking normal to regular visitors.
2. Redirects Traffic to a Malicious File
- RewriteRule ^(.*)$ hackfile.php?$1 [L] forces matching requests to be redirected to hackfile.php.
- This file likely contains malware, spam links, or phishing content.
To remove this,
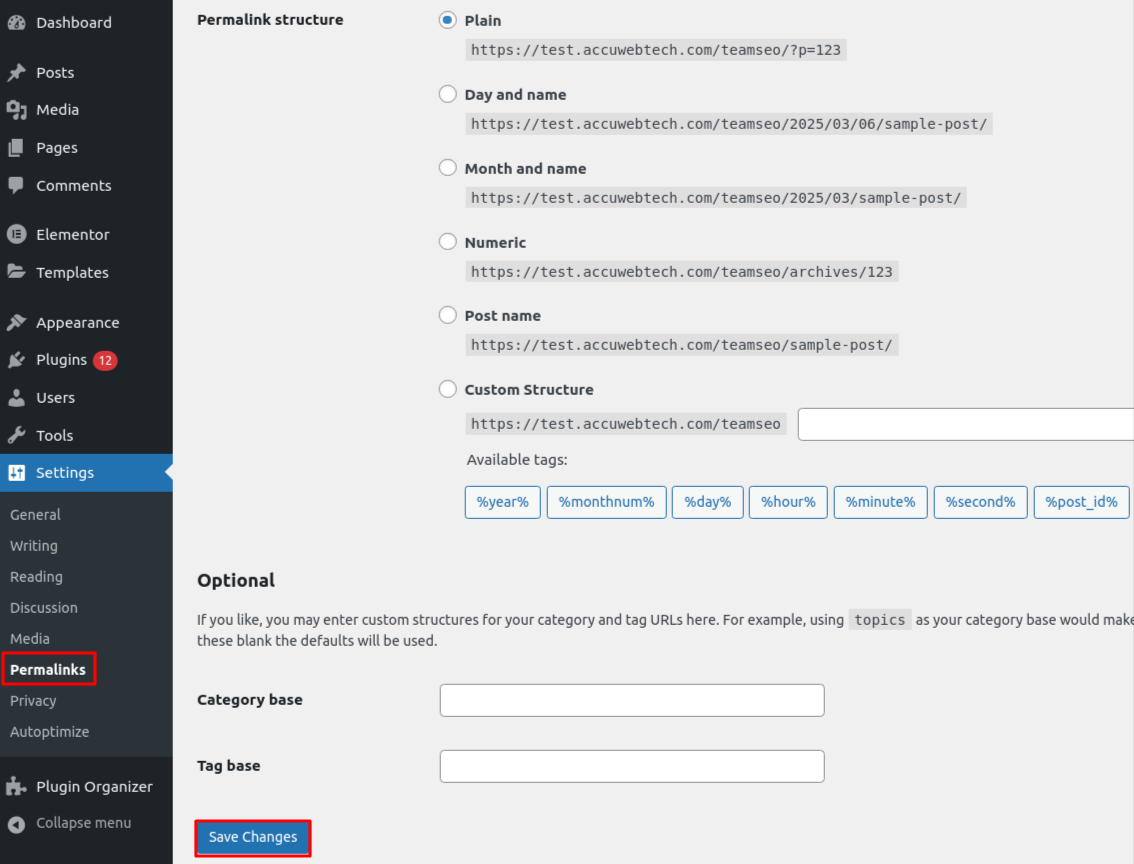
To reset your settings, delete the .htaccess file.
1. Log into your WordPress Dashboard.
2. Navigate to the Settings > Permalinks.
3. Without modifying, click on Save Changes.
(By default, WordPress regenerates the .htaccess file automatically.)
4. Clean Malicious Code From the Database
- Log into your cPanel account.
- Navigate to the Databases > phpMyAdmin.
- Choose your database.
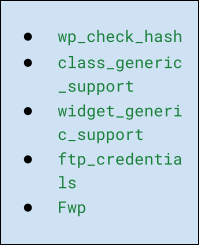
- Open the wp_options table.
- In the Search tab, search for the texts below, if found then delete it.

5. Change the Passwords
Changing the passwords for WordPress, FTP, databases, and your hosting panel is crucial to securing your site after a hack or potential security threat.
The WordPress admin password should be updated to stop hackers from logging in. The FTP and database passwords should also be changed because hacks can be used to inject malware or manipulate website data.
Finally, the hosting panel password needs to be updated, as it grants access to all server files, settings, and email accounts.
6. Ask Google to Recrawl Again
Inform Google about the recent changes by:
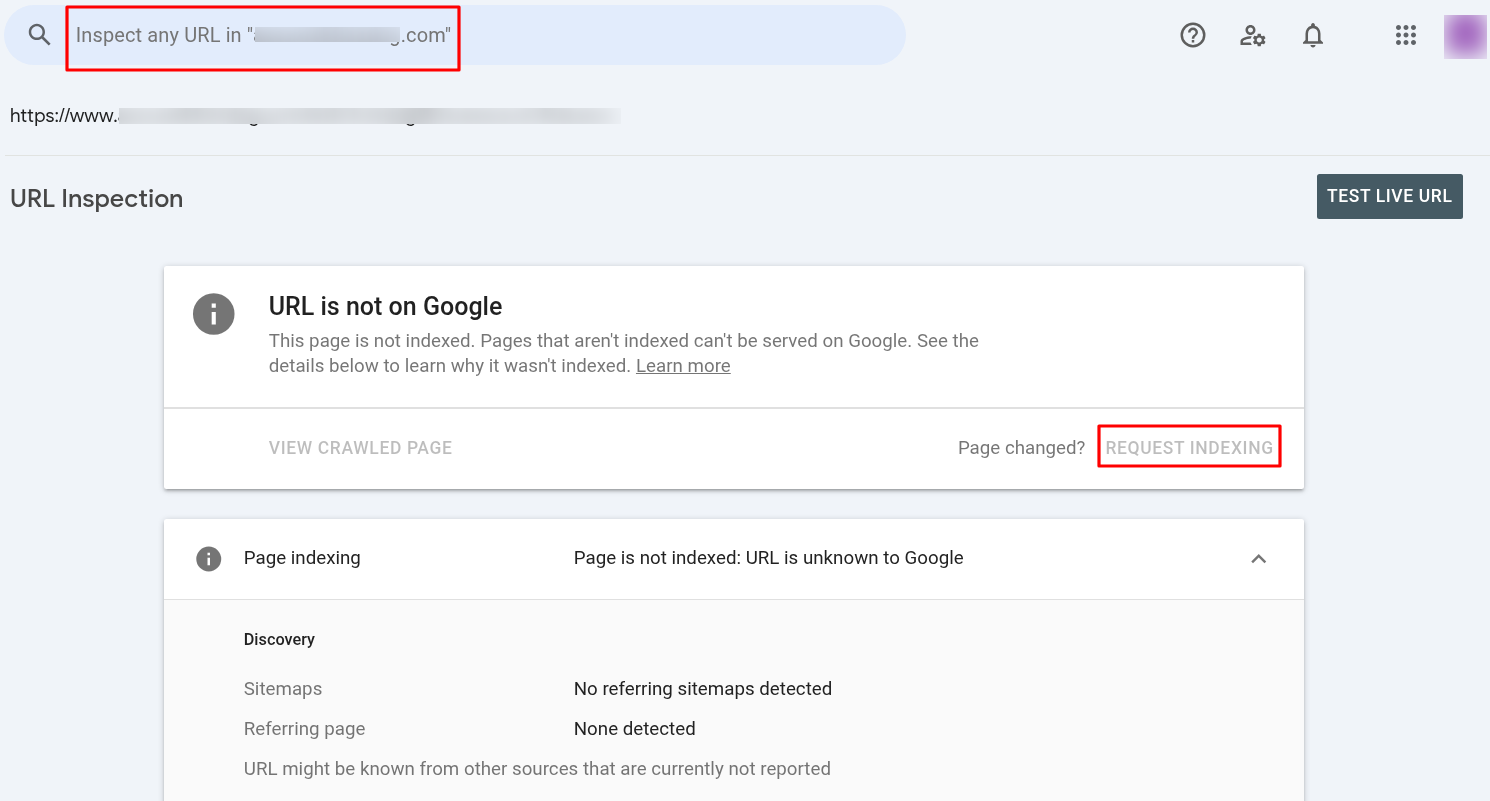
1. Inspect and Request Indexing for Individual URLs:
- Log into Google Search Console.
- In the top search bar, enter the full URL of the page you want Google to re-crawl and press Enter.
- The URL Inspection Tool will display the page's current index status.
- If the page has been updated or was previously affected by a hack, click on the "Request Indexing" button to prompt Google to re-crawl and re-index the page.
2. Resubmit Your Sitemap:
- Next, click on "Sitemaps" under the "Index" section.
- In the "Add a new sitemap" text, enter the URL of your sitemap (e.g., sitemap.xml) and click "Submit".
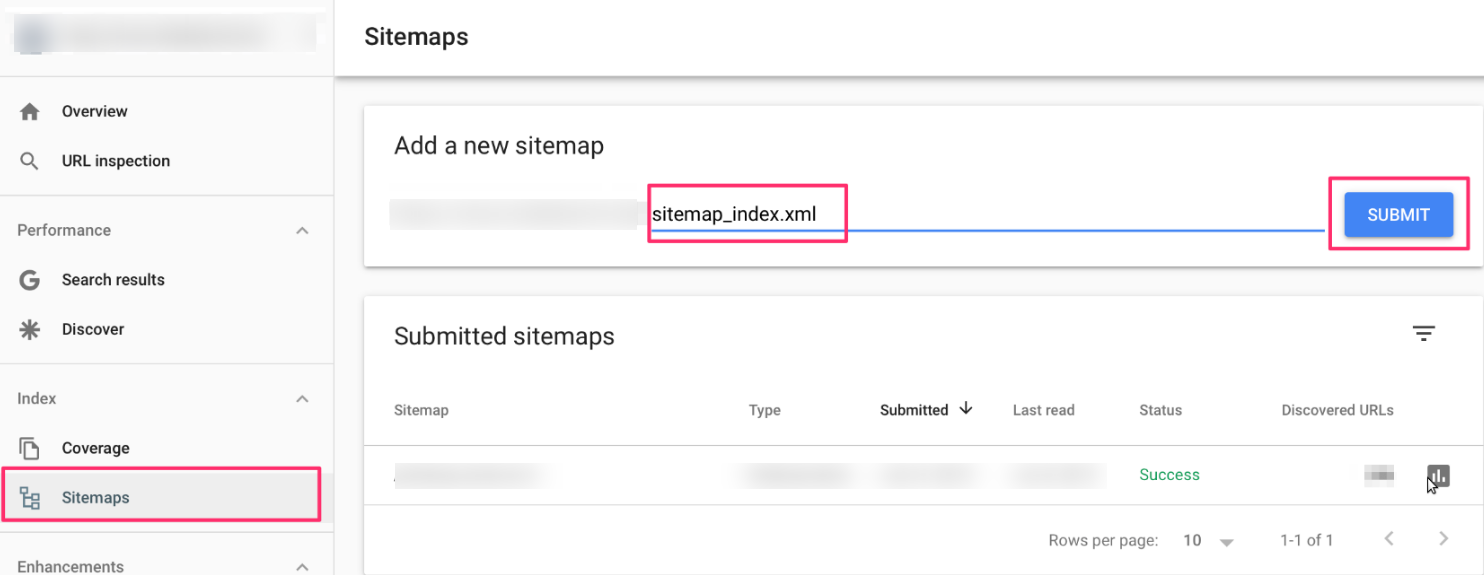
Resubmitting your sitemap helps Google discover and index multiple pages efficiently.
3. Check for Manual Actions:
- Go to the"Security & Manual Actions" section, click on "Manual Actions".
- Make sure there are no hand penalties on your site. If there are, use the guidelines provided to rectify them and ask for a review.
Don't worry! We continuously monitor and protect your site from any attacks. Our team conducts regular audits on all servers to detect and fix any hardware or performance issues.



