What is SSRF?
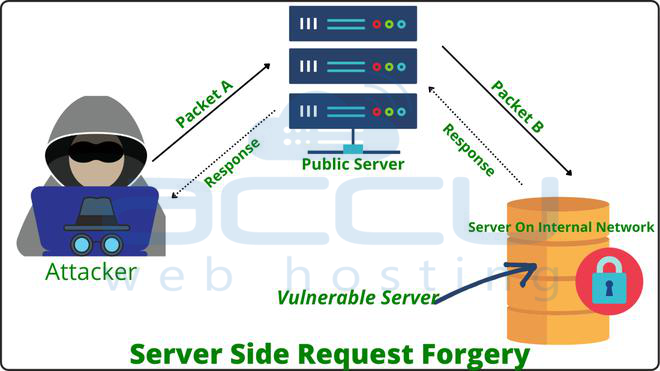
A Server-Side Request Forgery (SSRF) security flaw allows a hacker to deceive a server into accessing undesired resources on his behalf.
The "Unauthenticated Blind SSRF via DNS Rebinding" warning suggests that your WordPress version may have a flaw that enables an attacker to use the DNS rebinding technique to forge requests from your WordPress server to other resources, possibly internal services, without the need for any authentication. This might be exploited to access confidential data or take advantage of other server flaws.
This is because of a race condition known as Time-of-Check-Time-of-Use (TOC-TOU) between HTTP requests and validation checks, allowing URLs to be validated and modified before being used by the software. Because of this, an attacker can expose hosts that should not be reachable on a server by altering the domain in a pingback request to link to a different address from the one previously authenticated.
DNS Rebinding
DNS rebinding is a method that misleads a victim's browser into sending queries to a domain that resolves to a different IP address, depending on the time of the request. A security measure known as the "same-origin policy" prevents web pages from sending requests to domains other than the one that was originally supplied.
A malicious website that first responds to an attacker-controlled IP address but later switches to resolve to the IP address of an internal network resource is created as part of a DNS rebinding attack. This enables the attacker to deceive the victim's browser into sending requests to restricted internal resources.
How to fix the security warning "WP <= 6.1.1 – Unauthenticated Blind SSRF via DNS Rebinding"?
1. Update the WordPress core
Make sure the most recent version of WordPress is installed on your website. Updating your software is essential because vulnerabilities are frequently patched in subsequent editions.
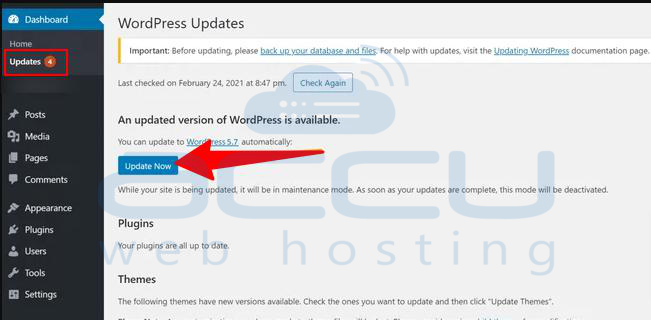
Step 1: Log into your WordPress Dashboard.
Step 2: Select Updates; you have the latest version notification on this page.
Step 3: Click on Update Now.
2. Update themes and plugins.
Ensure all of your plugins and themes are updated. It is possible to carry out attacks or acquire unauthorized access by taking advantage of vulnerabilities in plugins and themes.
Update plugins:
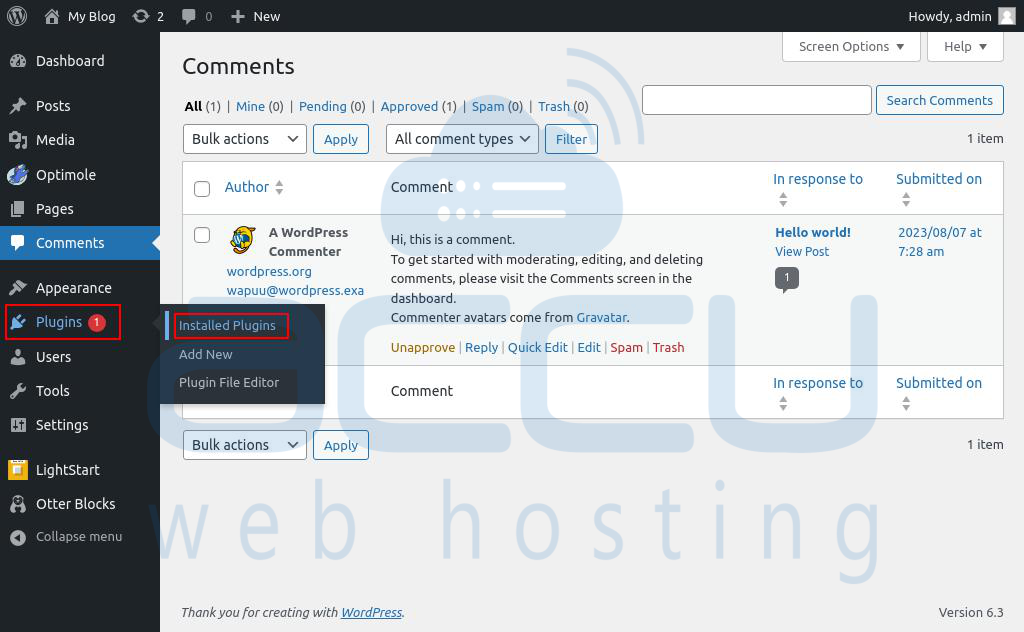
Step 1: Log into your WordPress Dashboard.
Step 2: Go to the Plugins > Installed plugin.
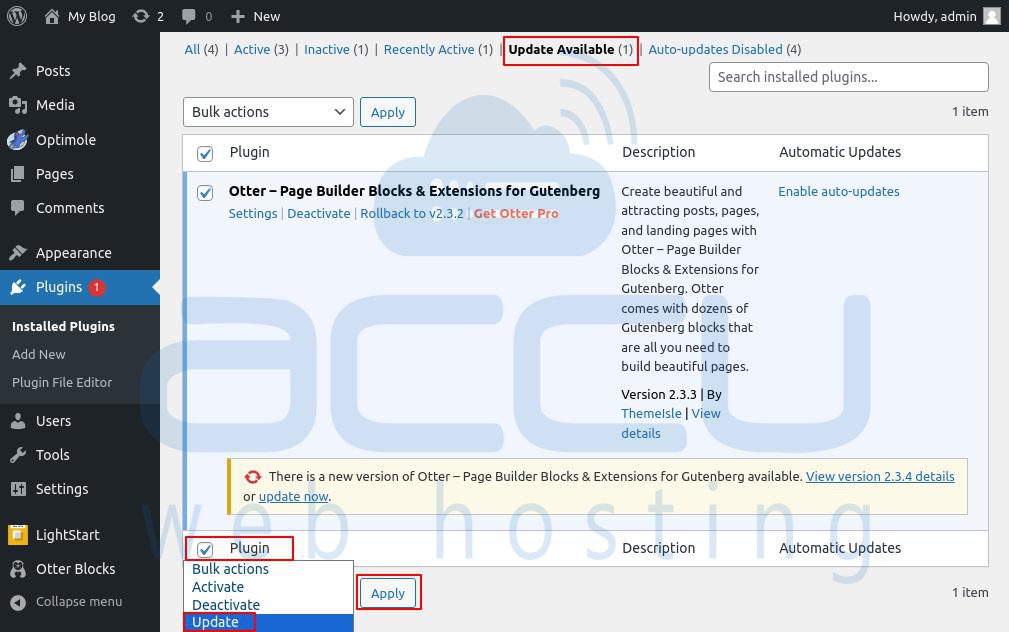
Step 3: On this page, choose Update Available.
Step 4: Select the plugin, choose the Update option from Bulk Action Dropdown.
Step 5: Click on Apply.
Update Themes:
Step 1: Log into your WordPress Dashboard.
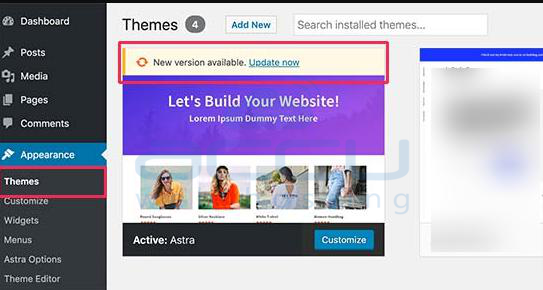
Step 2: Navigate to Appearance > Themes.
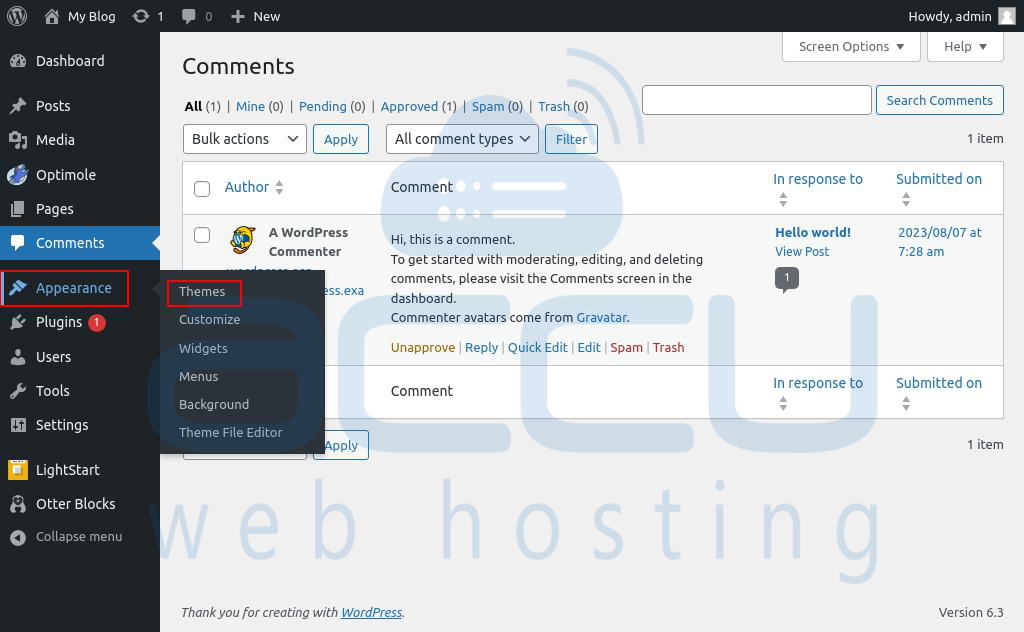
Step 3: On this page, click on Update Now on your active theme.
Update plugins and themes from the Dashboard
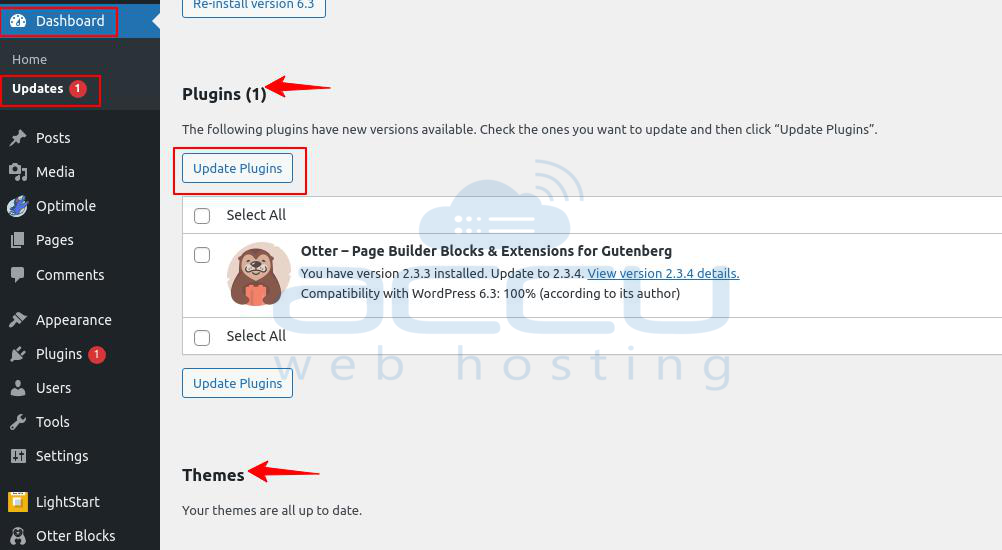
Step 1: Go to wordpress Dashboard.
Step 2: Select the Updates option.
Step 3: On this page, you get a button for plugins and theme updates.
3. Remove Unnecessary Themes and Plugins:
Any plugins or themes that are no longer in use should be removed. Unused or obsolete plugins and themes may increase your WordPress site's attack surface.
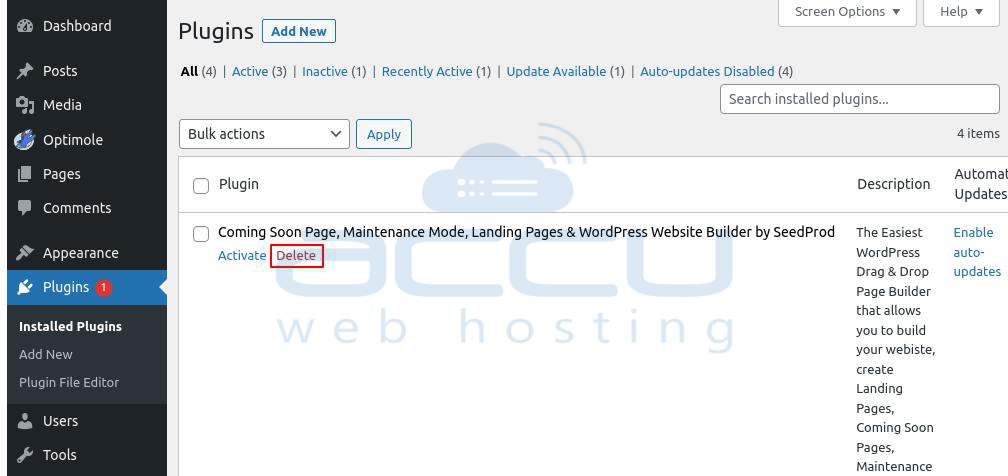
Remove Plugin
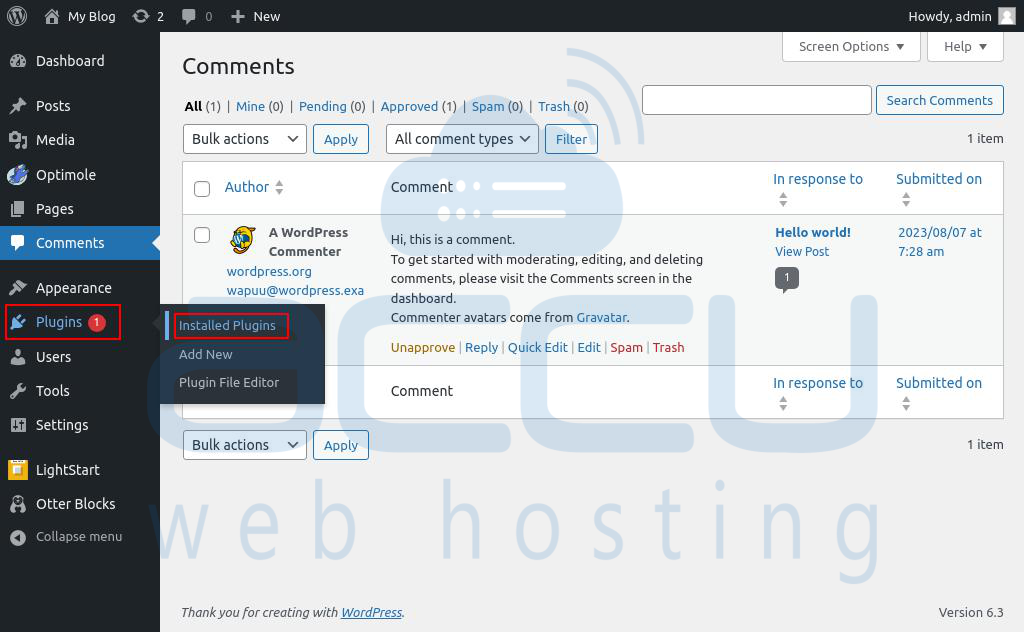
Step 1: Log into your WordPress Dashboard.
Step 2: Go to the Plugins > Installed plugin.
Step 3: Select your unnecessary plugin and click on Delete to remove it.
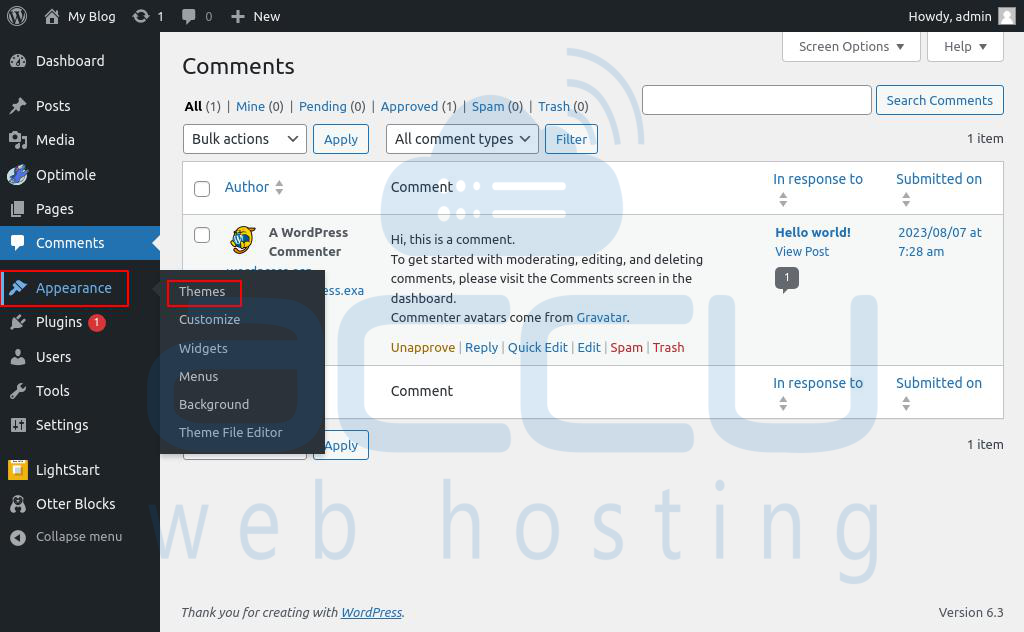
Remove Themes
Step 1: Log into your WordPress Dashboard.
Step 2: Navigate to Appearance > Themes.
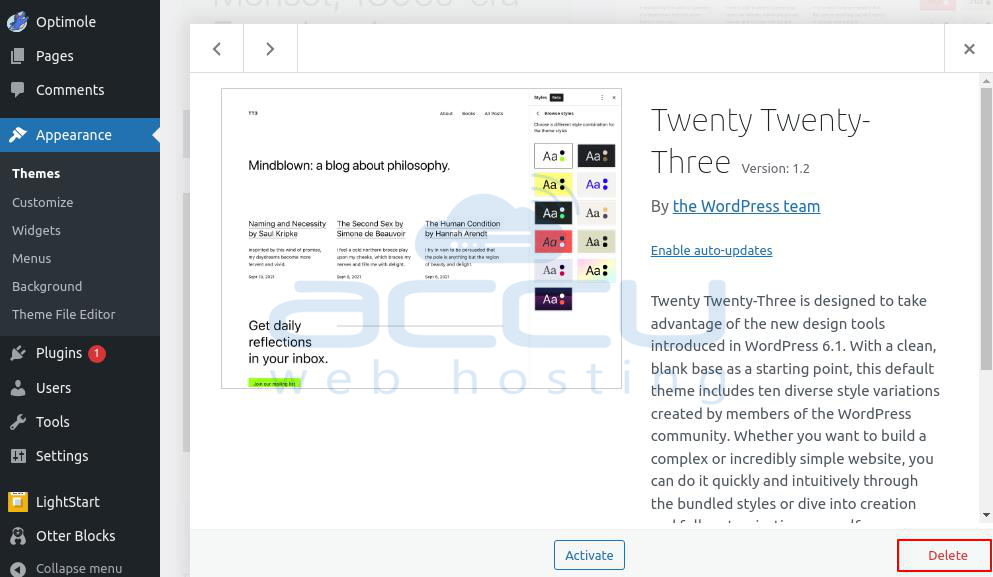
Step 3: Select your unnecessary theme and Delete it from the page's bottom-right side.
4. Use a Security plugin
Choose a security plugin that will assist you in identifying and reducing potential risks. Plugins like Wordfence or Sucuri Security can offer a defense against SSRF and other types of attacks.
Step 1: Log into your WordPress Dashboard.
Step 2: Navigate to Plugins > Add New.
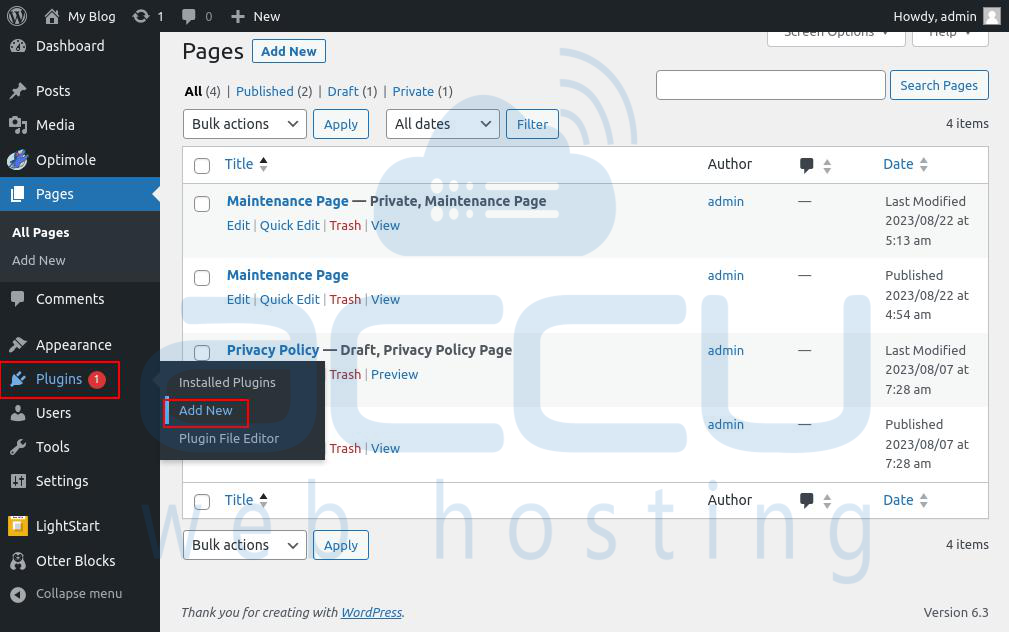
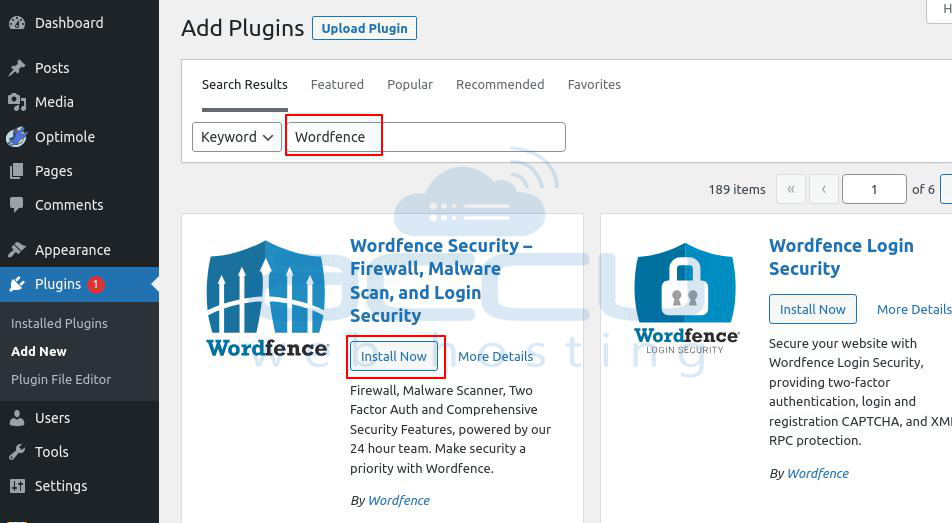
Step 3: On this page, search for security plugins (e.g., Wordfence).
Step 4: Click on Install Now and activate that plugin by selecting the Activate button.
5. Web Application Firewall
Implement a web application firewall to filter incoming traffic and stop dangerous requests. This can provide further security against SSRF and other threats.
Step 1: Log into your WordPress Dashboard.
Step 2: Navigate to Plugins > Add New.
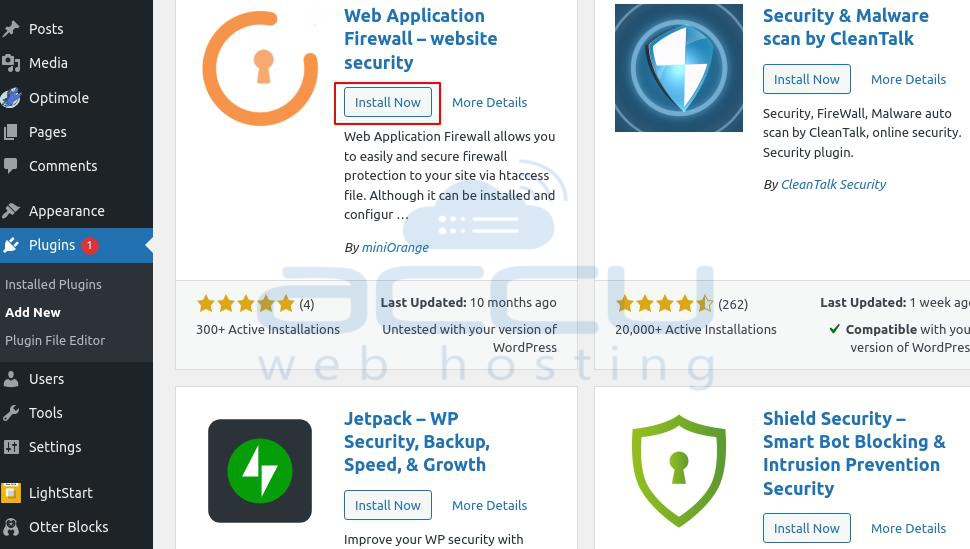
Step 3: On this page, search for a security plugin (e.g., Web Application Firewall).
Step 4: Click on Install Now & activate that plugin by selecting the Activate button.
6. Disable external requests
Limit outgoing Traffic: Set your server's firewall or security parameters to restrict outbound traffic from the server to resources outside the network. This can help stop future SSRF attacks from sending out illegal requests.
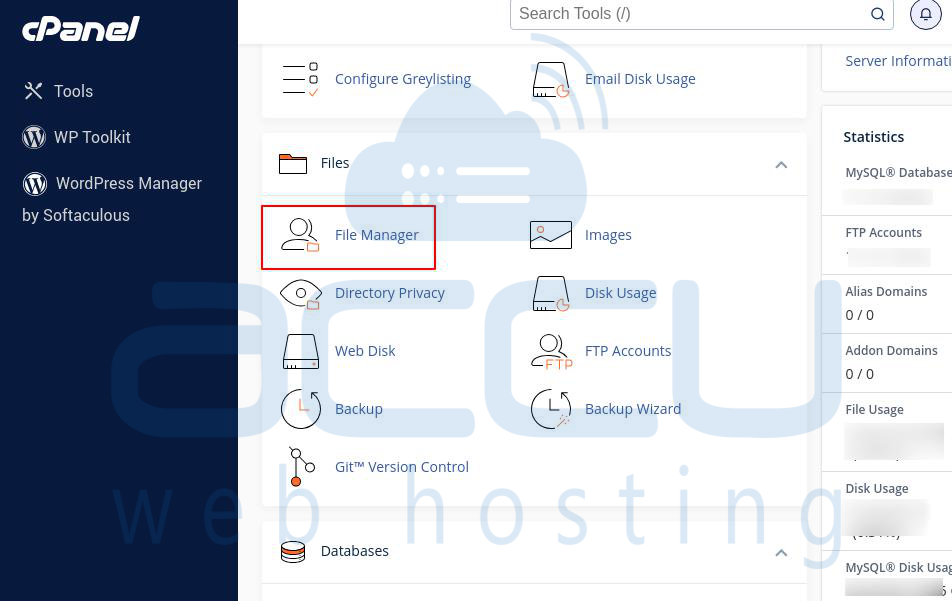
Step 1: Log into your CPanel account.
Step 2: Scroll down to Files and select File Manager.
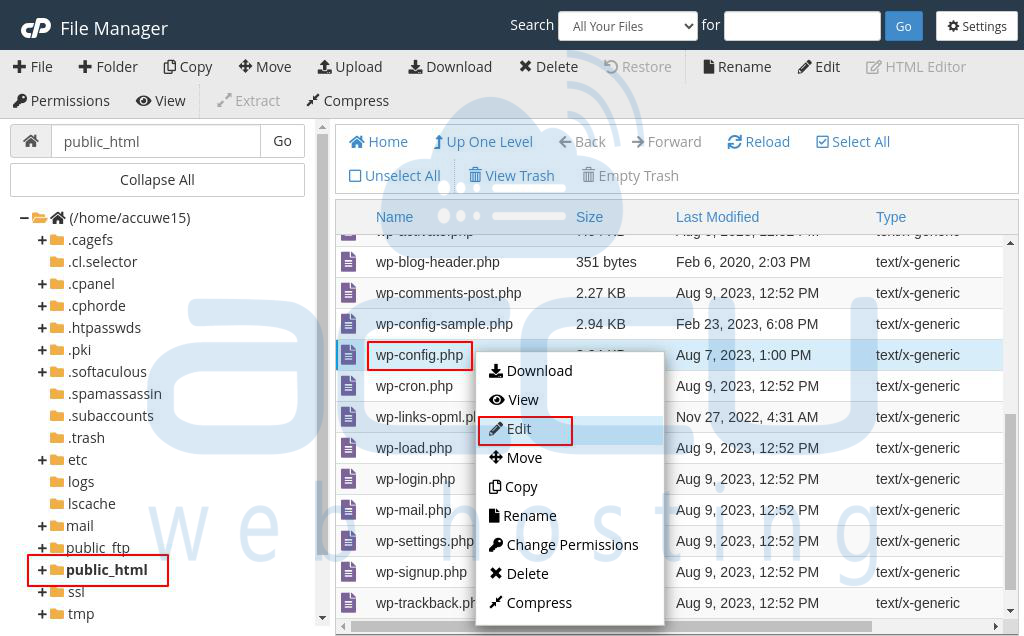
Step 3: Inside the public_html directory, search the wp-config.php file.
Step 4: Right-click on the wp-config.php file and choose Edit.
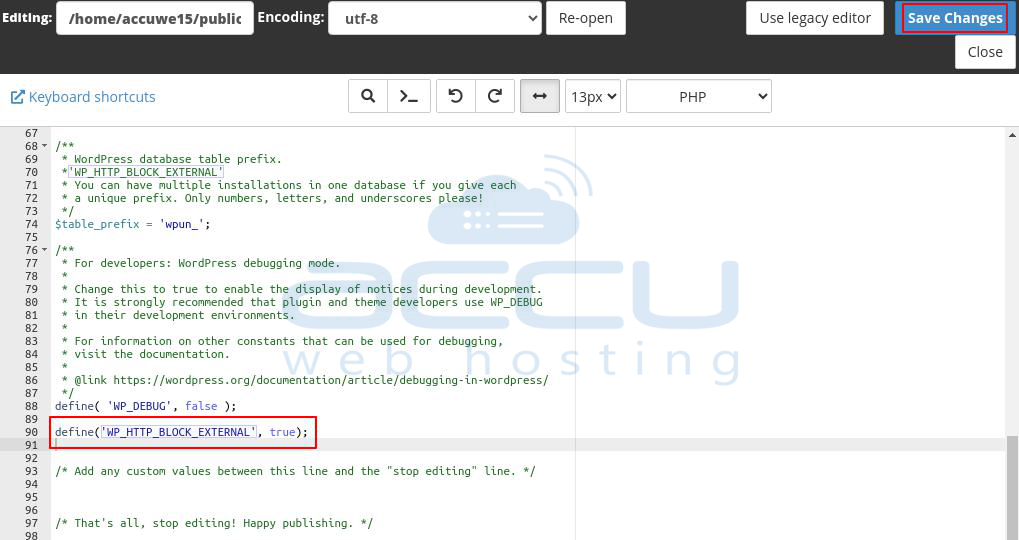
Step 5: Add the below code to disable external requests:
define('WP_HTTP_BLOCK_EXTERNAL', true);
Step 6: Click on Save Changes.
7. Input Validation and Escaping
It's important to consider how WordPress handles incoming data and how users will see it when building theme and plugin code.
On the other end of the security scale, Escaping handles security. To escape, secure any data you may already have before delivering it to the user. Escape everything from untrusted sources (e.g., users and Databases), third parties (e.g., Facebook), etc. For escaping, use the esc_html() function.
<h2><?php echo esc_html($title); ?></h2>
8. Backup and Recovery
Make regular backups of your WordPress website's database. The ability to restore your site to a known good condition after a security breach is made possible by having recent backups.
Conclusion
To protect your WordPress site against potential exploitation, you must take urgent action in response to the security alert "WP = 6.1.1 - Unauthenticated Blind SSRF via DNS Rebinding." This flaw enables attackers to use DNS rebinding to launch an unauthenticated Server-Side Request Forgery (SSRF) attack. Consequences include unintentional acts on your server or unauthorized access to critical data.



